Security Controls
The bad actors are look at different way that they can get access to our systems. SO, as a security professional, we have to make sure we are protecting all aspects of our organization from building to people to systems. We have to consider assets, which might be physical assets like hardware, data, software inventory etc. Now, in order to protect all these different assets of different kinds, there are different security controls we can implement that will cover most of an organizations bases to limit any damage.
The following are the broad categorization of the these controls:
- Technical Controls :: Controls implemented using systems like OS, firewall, anti virus etc
- Managerial Controls :: Controls associated with security design and implementation like security policies, standard operating procedures etc.
- Operational Controls :: Controls implemented using people like security gaurds, awareness programs etc
- Physical Controls :: Limiting Physical access, Guard Shack, Fences, locks, Badge readers.
All the aforementioned controls have different types of control types assiciated with them. All the differnet control types are mentioed below along with some examples of where what they might look like
- Preventive Control :: Limiting an access to a resources like a firewall or gaurd shack to check people’s identity entering to a building
- Deterrent Controls :: This might not prevent people from attacking but might scare/deter someone who has malicious intent.
- Detective Controls :: Detecting any potential attack that might be happening. Like reviewing logs or looking at tapes to suspicious activity or motion control sensors.
- Corrective Controls :: After an event has occured, to these controls help us to continue BAU activities without any business impact or minimal downtime. These controls may include backing up systems can mitigate ransomewaree, create policies for reporting security issues etc.
- Compensating controls :: We use compensating control types in cases where an event has occured but we do not have resources to be able to reverse damages that event casued. this might be on an temporary fix until we can get a long term solution
- Directive Control :: Direct a subject towards security compliance. This is relatively weak control. For Example: store all sensitive files in protective folder or signs that says
authorized personal only, which lets individuals to decide if they are allowed to walk into a door.
The follwoing table outlines some of the examples of each control and different control types:
| Preventive controls | Deterrent Controls | Detective Controls | Corrective controls | Compensating Controls | Directive Controls | |
|---|---|---|---|---|---|---|
| Technical | Firewall | Splash Screen | System Logs | Backup Recovery | Block instead of patch | File Storage Policies |
| Managerial | Onboarding Policy | Demotion | Review Login Reports | Policies for reporting issues | Seperation of duties | Compliance Policies |
| Operation | Guard Shack | Reception Desk | Property Petrols | Contact autorities | Require multiple security staff | Security policy Training |
| Physical | Door lock | Warning Signs | Motion detectors | Fire Extinguisher | Power generator | Sign: Authorized personal |
CIA Traid
The CIA Traid is at the core of all security. C stands for Confidentiality I stands for Integrity and A is for Availability.
Confidentiality is making sure that the data that is highly available is confendial to the users that only have access to it. This is most often done using Encryption. Also, need to know access and two factor authentication mechanisms also ensure that the information is confidential and is only accessable if the user has access to it. Integrity is to verify that the data is originated from the intended user/sender. Some of the Integrity process include Hashing, Digital Sign, Certificates and Non-Repudiation (which means we have proof of integrity and can confirm that information is coming from an expected user) Availability is highly important part of the traid. Redundancy, Fault Tolerance, patching all fall under this leg which makes sure that the systems are always available for the users to access data.
Non Repudiation
This is like signing a contract, there is no going back. The follwoing two proofs are needed for us to have non repudiation
- Proof of Integrity :: Ensuring that data that is being sent is not corrupted and can be verified using hash or MD5. But this doesn’t verify who sent this data.
- Proof of Origin :: Proving the source of the message like authentication.
We use a digital signature to provide this non repudiation, like using a pen and paper to sign a contract. With digital signataure, we use a private key to sign which can be verified using the public key of the user.
Authentication, Authorization and Accounting
Authentication proves who we say we are then Authorization decides the authorization they have to the resources and finally Accounting refers to the resources that were used during the time of the access. In most of the organization all the information related to AAA like crendentials, passwords etc are stored in a seperate AAA servers.
How to confirm if a system is authorized to communicate within our internal network? This can be done by using a certificate. In order to create this certificate, we need to have a CA(Certificate Authority), who will sign all the certificates that an organization can use. This CA will have a certificate signed by a root CA.
An Authorization model should be able to scale up when the capacity increases. Adding an abstraction ,like a groups that any number of users can be a part of, to provide access to a certain resource.
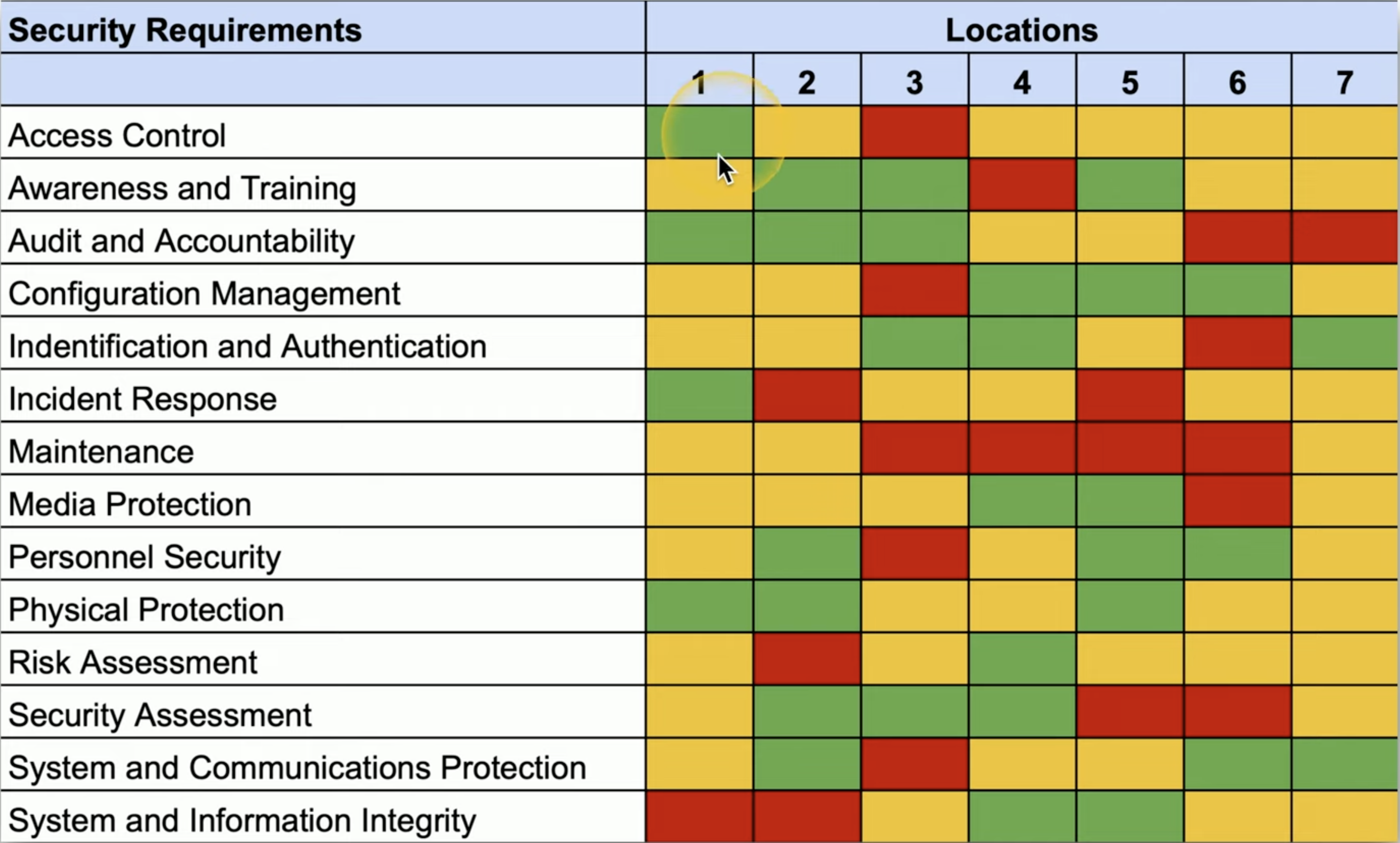
GAP Analysis
Where we are in term of security along with where we are headed against where we want to stand at the end of it. Before starting this analysis, it is good to have a baselines. There are NIST Special Edition Publication 800 171 Revision 2 or ISO/IEC 27001 etc will give a good idea on how a baseline should look like. we can also create our own baselines based on the needs of the organization.
- Get a baseline
- Examine the current processes
- The Comparision
- Identify Weakness against most effective processes
- A Details analysis by breaking each down to a smaller chunk. Visit NIST SP 800-53 to how this break down works.
- Final document that summarizes and the comparison of today vs where we need to be
- How to get to the desired state
- GAP analysis with the path, recommendation and time to it would take.